Understanding DHCP Snooping and Basic Configurations : Cisco, Juniper and Huawei - Route XP Private Network Services
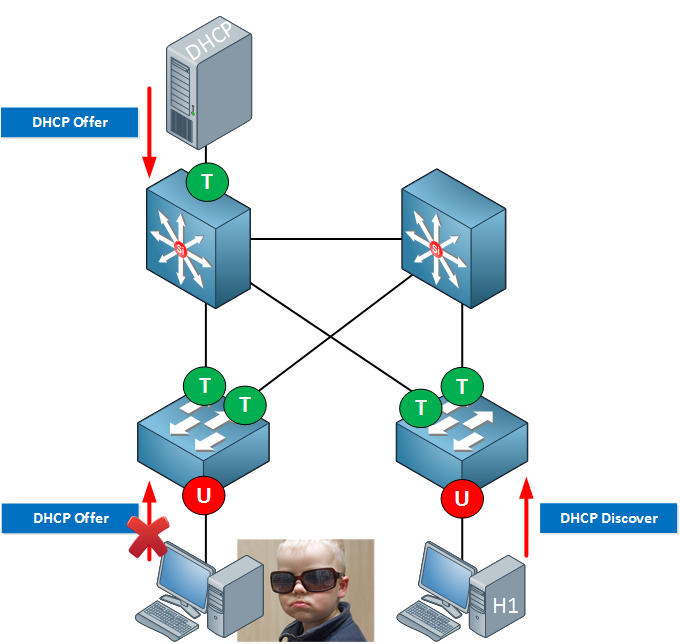
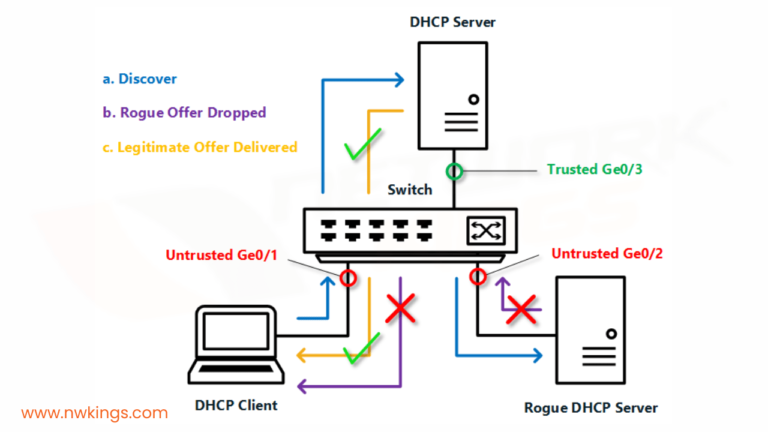
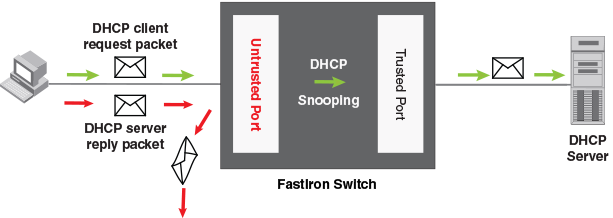
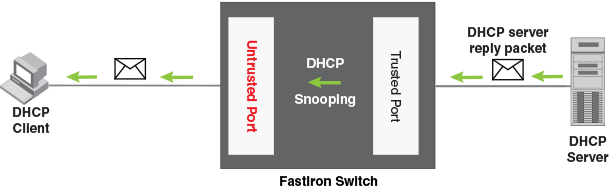
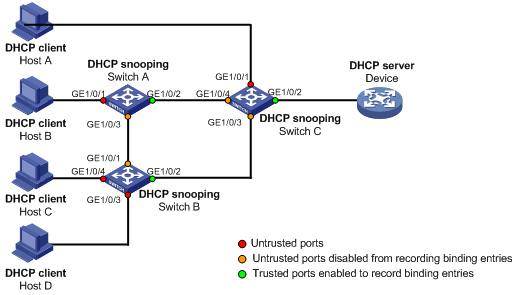
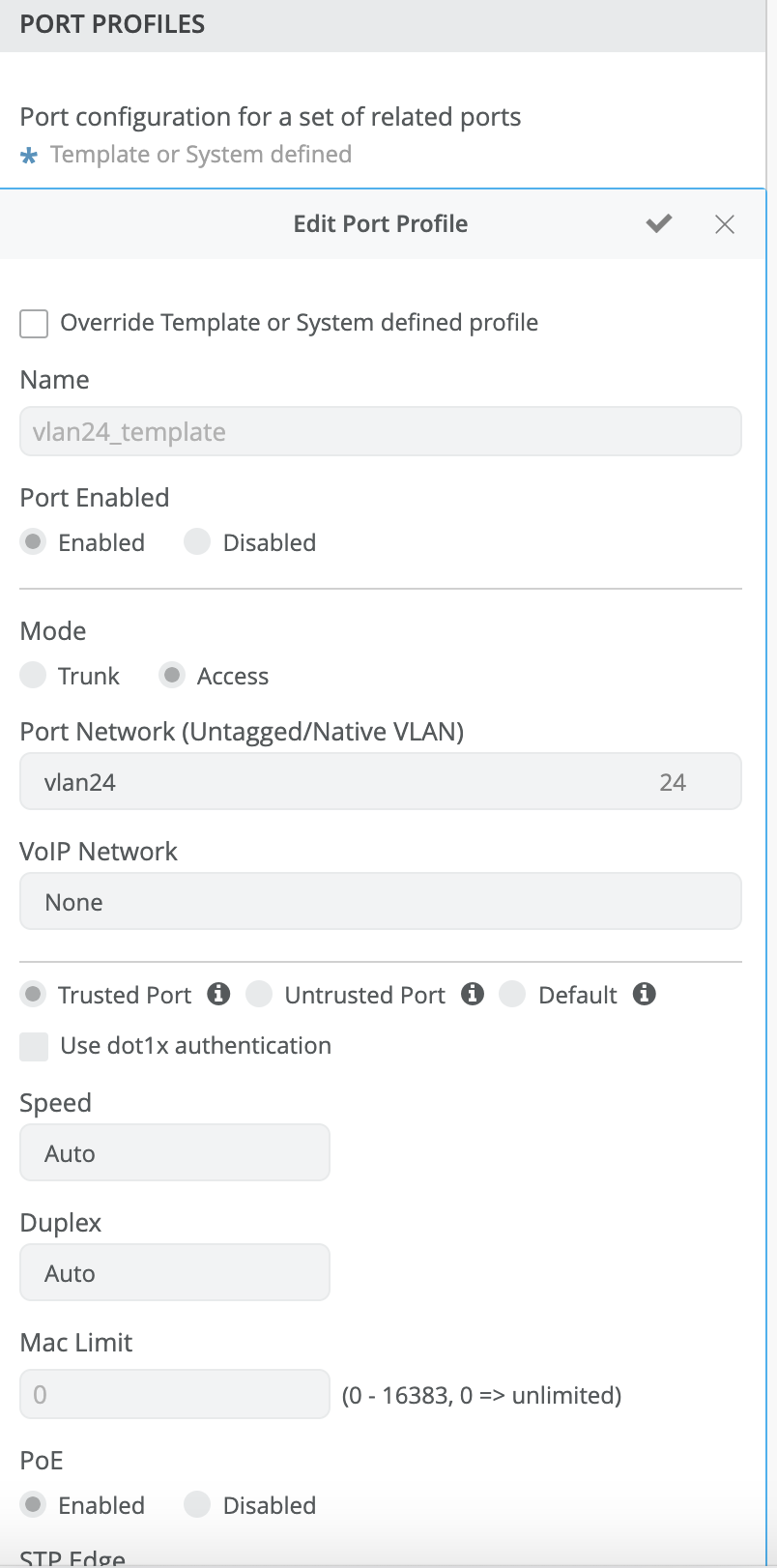
Complete Guide to DHCP Snooping, How it Works, Concepts, DHCP Snooping Database, DHCP Option 82, Mitigating DHCP Starvation Attacks, DHCP Hijacking, Man-in-the-Middle Attacks & Rogue DHCP Servers
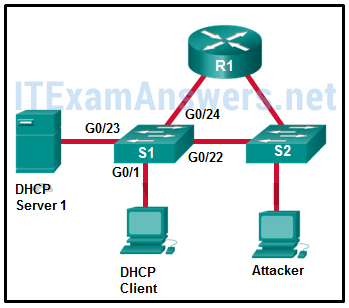
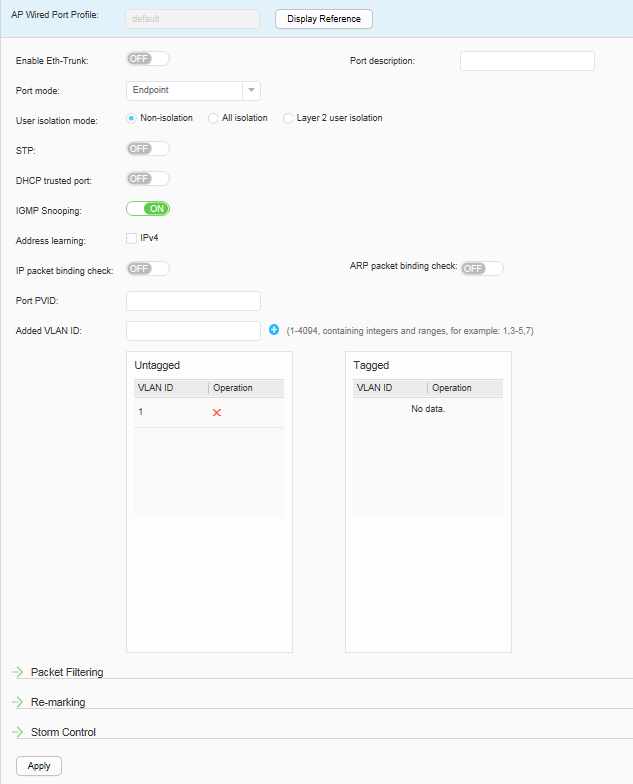
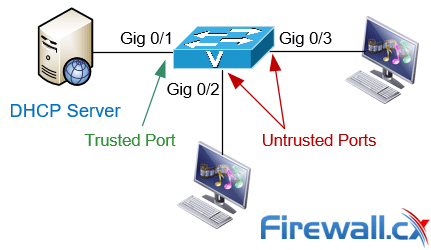
Refer to the exhibit. Which interface on switch S1 should be configured as a DHCP snooping trusted port to help mitigate DHCP spoofing attacks?

Switch Security: Management and Implementation (2.2) > Cisco Networking Academy's Introduction to Basic Switching Concepts and Configuration | Cisco Press